-
What is VXLAN?
VXLAN, which stands for Virtual Extensible LAN, is a network virtualization technology that allows the creation of virtualized Layer 2 networks over an existing Layer 3 infrastructure. It was developed to address the scalability limitations of traditional VLANs (Virtual Local Area Networks) in large-scale data center environments.
VXLAN encapsulates Layer 2 Ethernet frames within Layer 3 UDP (User Datagram Protocol) packets, enabling the extension of Layer 2 segments across Layer 3 boundaries. This allows for the creation of logical networks or overlays that can span multiple physical network devices, data centers, or even geographical locations.
Key features and benefits of VX include:
- (1) Scalability:
VXLAN uses a 24-bit segment identifier called the VXLAN Network Identifier (VNI), which allows for up to 16 million unique virtual networks, compared to the limited 4,096 VLANs in traditional Ethernet networks.
- (2) Multi-tenancy:
VXLAN enables the isolation and segmentation of network traffic for different tenants or applications, providing enhanced security and flexibility in multi-tenant environments.
- (3) Network virtualization:
By decoupling the logical network from the underlying physical infrastructure, VXLAN facilitates the creation of virtual networks that can be provisioned, managed, and migrated independently of the physical network.
- (4) Overcoming Layer 2 domain limitations:
VXLAN extends Layer 2 connectivity across Layer 3 boundaries, enabling the seamless movement of virtual machines (VMs) and workloads between different physical hosts data centers without the need for manual reconfiguration.
- (5) Compatibility:
VXLAN is designed to work with existing IP networks and leverages standard networking protocols such as UDP and IP, making it compatible with a wide range of networking equipment and software.
VXLAN has gained popularity in modern data center architectures, particularly in cloud computing and virtualized environments, where flexible and scalable network virtualization is essential to support the dynamic nature of workloads and applications.
-
Communication mode of VXLAN
(1) Routing mode: Communication between different network segments
- End to End communication:
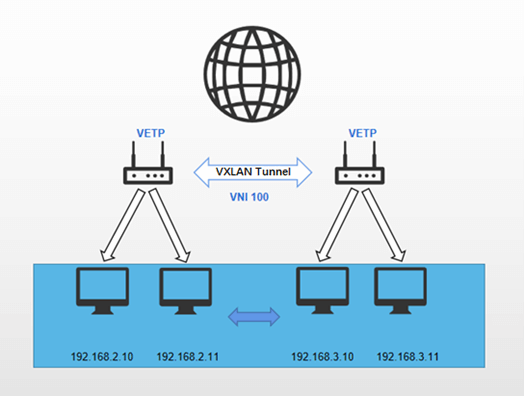
The two end devices establish a direct VXLAN tunnel, through which all data traffic is transmitted. The subnets on both devices form a unified Layer 2 subnet.
- Multiterminal forward communication:
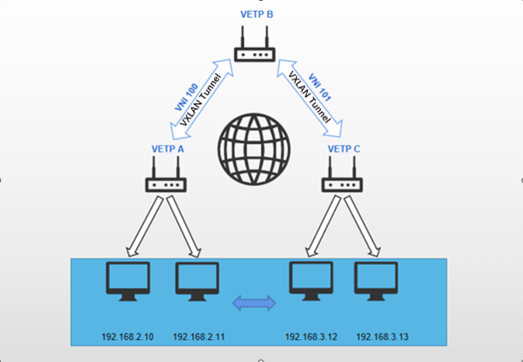
The objective is to establish a VXLAN tunnel between Device A and Device B, while simultaneously enabling Device C to also establish a VXLAN tunnel with Device B. This configuration facilitates the formation of a unified layer 2 subnet for the devices within subnets under both Device A and Device C, requiring potential data forwarding through multiple tunnels to reach its intended destination.
(2) Bridge mode: Communicates with a Network Segment
- End to End communication:
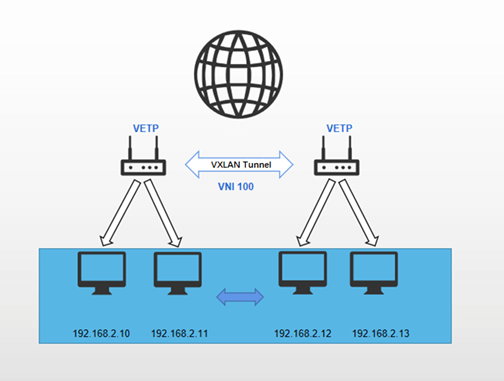
The two end devices establish a direct VXLAN tunnel, through which all data traffic is transmitted. The subnets on both devices form a unified Layer 2 subnet.
- Multiterminal forward communication:
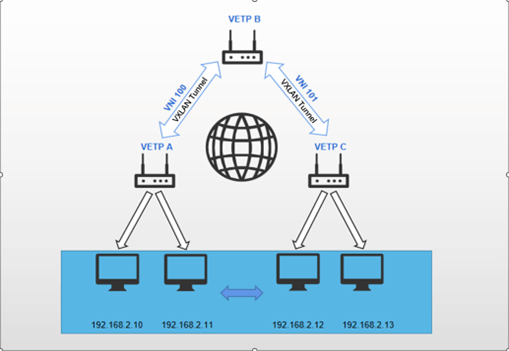
Establish a VXLAN tunnel between Device A and Device B, while also configuring a VXLAN tunnel between Device C and Device B. This configuration enables the subnet devices under both Device A and Device C to form a unified layer 2 subnet, with data potentially being forwarded through multiple tunnels in order to reach its intended destination.
-
VXLAN vs VLAN
VXLAN (Virtual Extensible LAN) and VLAN (Virtual Local Area Network) are both network technologies used to segment and isolate traffic within a network, but they operate at different layers of the networking stack and have distinct characteristics. Here’s a breakdown of the differences between VXLAN and VLAN:
- (1) Layer: VLAN operates at Layer 2 of the OSI model, while VXLAN operates at Layer 3.
- (2) Scalability: VLANs are limited to 4,096 unique VLAN IDs due to the 12-bit VLAN identifier field in Ethernet frames. In contrast, VXLAN uses a 24-bit VXLAN Network Identifier (VNI), allowing for a much larger number virtual networks (over 16 million).
- (3) Encapsulation: VLAN tags are added to Ethernet frames by modifying the 802.1Q header, which adds a 4-byte VLAN tag. VXLAN encapsulates Ethernet frames within UDP packets, adding a 50-byte VXLAN header.
- (4) Addressing: VLANs use VLAN IDs to identify and separate traffic, typically assigned statically or through protocols like VLAN Trunking Protocol (VTP). VXLAN uses VNI values to identify virtual networks, and these values are dynamically assigned.
- (5) Spanning multiple Layer 3 domains: VLANs are limited to a single Layer 3 domain, requiring additional mechanisms like VLAN trunks or Layer 3 routing to extend them across multiple domains. VXLAN, on the other hand, can span multiple Layer 3 domains, enabling more flexible network designs and easier scalability.
- (6) Overlays: VXLAN is often used as an overlay network technology, allowing virtual networks to created and extended over an existing physical network infrastructure. VLANs, on the other hand, are typically used within a single physical network.
- (7) Multitenancy: VXLAN provides better support for multitenancy scenarios, where multiple customers or organizations share the same physical infrastructure while maintaining isolation. VXLAN’s larger address space allows for more granular segmentation and separation of traffic.
Overall, VXLAN designed to address the limitations of VLANs in terms of scalability, flexibility, and multitenancy. It is commonly used virtualized and cloud environments where there is a need for large-scale network segmentation and overlay networks.
-
VXLAN vs VPN
VXLAN (Virtual Extensible LAN) and VPN (Virtual Private Network) are both technologies used in networking, but they serve different purposes.
- (1) VXLAN:
VXLAN is a network virtualization technology that allows the creation of virtual Layer 2 networks over an existing Layer 3 infrastructure. It extends Layer 2 segments across Layer 3 boundaries by encapsulating Ethernet frames within IP packets. VXLAN is primarily used in data center environments to enable network virtualization and facilitate the creation of overlay networks. It helps overcome the limitations traditional VLANs by providing scalability, flexibility, and multi-tenancy support.
- (2) VPN:
A Virtual Private Network (VPN) is a secure connection established over a public network, typically the internet, that allows users access a private network remotely. VPNs provide encryption and authentication mechanisms to ensure the confidentiality and integrity of data transmitted between the user’s device and the private network.
Key features of VPNs include:
- (1) Secure remote access:
VPNs allow users to securely connect to a private network from remote locations, such as home or public Wi-Fi networks, by encrypt their traffic and establishing a secure tunnel.
- (2) Privacy and anonymity:
By encrypting data and masking the user’s IP address, VPNs provide privacy and anonymity, making it difficult for third parties to monitor or track online activities.
- (3)Site-to-site connectivity:
VPNs can also be used establish secure connections between different networks, such as branch offices or multiple data centers, creating a virtual private network over the public internet.
In summary, VXLAN is a technology for network virtualization and overlay networks within data center environments, while VPN is a technology for secure remote access and site-to-site connectivity over public networks like the internet.
-
What role will VXLAN play in IoT?
VXLAN (Virtual Extensible LAN) is primarily a network virtualization technology used in data centers to provide overlay networks. While VXLAN itself is not directly tied to IoT (Internet of Things), it can play a role in supporting IoT deployments in certain scenarios.
Here are a few ways VXLAN can be relevant to IoT:
- (1) Scalability:
IoT devices generate massive amounts of data, and as the number of devices increases, traditional network architectures may struggle to handle the scale. VXLAN can help address this challenge by providing a scalable overlay network that allows for efficient communication between IoT devices and gateways.
- (2) Segmentation and Isolation:
In IoT deployments, it’s often necessary to segment and isolate different types of devices or groups devices for security, performance, or management reasons. It enables the creation of virtual networks overlays, allowing for logical separation of IoT devices while sharing the same physical infrastructure.
- (3) Multitenancy:
In scenarios where multiple organizations or tenants share the same IoT infrastructure, it can facilitate multitenancy by providing isolated virtual networks for each tenant. This allows for secure and independent operation of IoT services for different entities on a shared infrastructure.
- (4) Mobility and Flexibility:
IoT devices can be mobile or deployed in dynamic environments. VXLAN’s overlay network approach can provide flexibility and mobility support by decoupling the logical network from the underlying physical infrastructure. This allows IoT devices to move across different physical locations or networks without requiring reconfiguration of the underlying network infrastructure.
It’s important to note that while VXLAN can offer benefits in certain IoT use cases, there are other networking technologies and protocols specifically designed for IoT, such as MQTT (Message Queuing Telemetry Transport) and CoAP (Constrained Application Protocol), which focus on lightweight messaging and resource-constrained devices. The choice of networking technology in an IoT deployment depends on various factors, including the specific requirements, scale, and constraints of the IoT solution.
Relevant Article:



2 Comments